How to Telnet in Linux: A Comprehensive Guide

Telnet is an old, insecure way of connecting remotely to a server. That being said, it can be useful, so let’s look at how to telnet in Linux in this guide.
In the early days of the Internet, when we wanted to log into a remote server, we used telnet. This communications protocol, which has been around since the late 1960s, is growing less popular in modern computing.
That’s largely for security reasons, but there may still be times when you need to use telnet in Linux. Read along as I show you how and why to use this admittedly archaic way of logging into computers you don’t have physical access to.
A Brief History of Telnet
Telnet, which stands for “Teletype Network,” traces its roots back to the late 1960s. Developers wrote telnet as a protocol that allowed different time-sharing systems to communicate with one another.
The primary goal was to facilitate remote login capabilities over the nascent ARPANET, the precursor to today’s modern internet.
Telnet’s primary function was to emulate a terminal. It makes it look like you’re at a terminal directly attached to a remote system. This was particularly valuable for accessing distant mainframes and shared computer resources. Back in the day, most of us configured our web servers and wrote our web pages using telnet.
The Difference Between Telnet and SSH
Telnet, like I said from the beginning, is waning in popularity. That’s mainly for security concerns: telnet sends all of your information (even your username and password) in plain text. It’s definitely not a good idea in almost any scenario.
On the other hand, SSH is encrypted and sends virtually nothing in plain text. Furthermore, SSH is extensible and can utilize stronger encryption methods as they become available. In a nutshell, if you can use SSH instead of telnet, you really should. If, however, you really need to use telnet, let’s walk through how to do so.
Setting Up Your Linux Environment for Telnet
Quite often on modern Linux distributions, you won’t find telnet installed by default. That means you’ll need to install it using your package manager of choice.
To find out if telnet already exists, just issue the following command from your Linux terminal:
$ which telnet

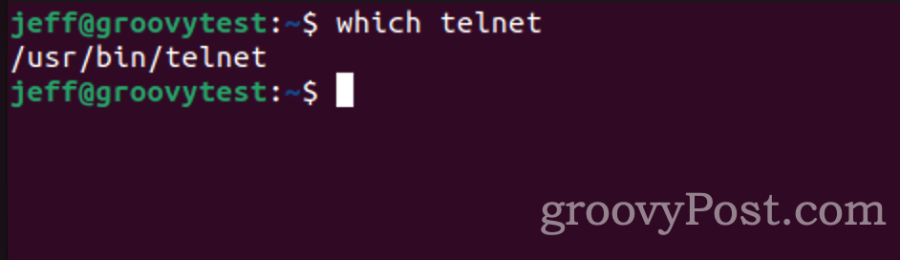
On my Ubuntu installation, telnet is located at /usr/bin/telnet, and which promptly tells me that. If all you get in response is the command line again, with no directory and file listing, you don’t have telnet installed.
To fix that, we’ll fire up our package manager. In Ubuntu and other Debian-based systems, you’ll install telnet using the following commands:
$ sudo apt update $ sudo apt install telnet
Fedora, CentOS, and other distributions use yum for package management, instead. Here’s how to install the telnet package on those distributions.
$ yum -y install telnet
That accomplished, it’s time to learn how to actually use telnet.
How to Use Telnet in Linux
In its most basic usage, all you do is type the telnet command followed by the hostname or IP address you’re logging into. For example:
$ telnet localhost
The preceding command would establish a telnet connection using the default port to your own local Linux computer. Often, though, you’ll need to specify which port to use. In that case, you simply add the port number after the hostname or IP address.
$ telnet resort.org 2323


That command would connect you to a venerable chat server known as The Resort Online, found on port 2323 of resort.org.
One of my oldest online hangouts from my first days as an internet user, The Resort is purely text-based. That’s why it uses telnet. That particular server has always used port 2323 for connections.
The Importance of Port Numbers in Telnet
Of course, that’s a non-standard port, open for use by non-system software. A number of server packages use specific ports of the TCP and UDP protocols. For example, your standard web server communicates everything over port 80.
Ports are like street numbers for your house or business. The hostname or IP address is the street name, like Main Street. The port is where on Main Street that particular program lives.
A few other commonly-used ports include:
- 22: used for the SSH protocol.
- 25: commonly used for outgoing mail servers.
- 80: used by most web servers.
- 220: Commonly used by IMAP email servers.
- 443: Secure web servers often use this port.
As illustrated above, you can specify which port you want to connect to simply by typing it after the hostname or IP address in your telnet command.
Utilizing Telnet for Network Diagnostics
With that information in mind, it becomes easy to see why telnet can still be an important tool for network and system administrators. When a mail or web server seems to be misbehaving, it proves useful to telnet into that server for troubleshooting and diagnostics.
You can use telnet to ensure the server in question is accepting connections, for example. Let’s say you need to check if a web server is accepting connections on port 80:

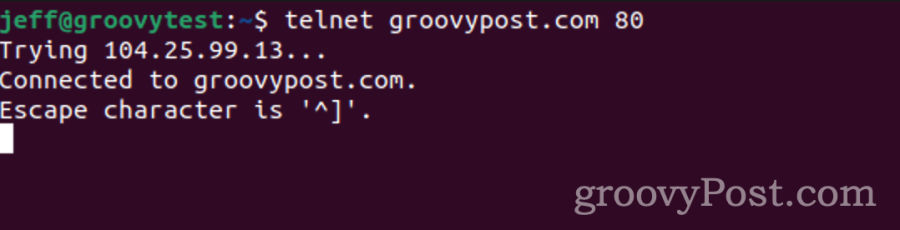
You can also use telnet to manually send emails through SMTP, which can be helpful for debugging mail server issues. By connecting to port 25 (SMTP) and entering proper SMTP commands, you can simulate the process of sending an email and see responses from the mail server in real time.
The Security Concerns with Telnet
While telnet is a valuable tool for network troubleshooting due to its manual and straightforward nature, it’s important to use it responsibly. Since telnet does not encrypt its traffic, any sensitive information sent over telnet (like your password) can be intercepted.
Always be cautious about where and how you use telnet, especially in production or sensitive environments. Really, you should only use telnet when you have to or when the computer is completely unexposed to external security threats.
Why Telnet Still Exists in Today’s Computing Environment
Even with the rise of more secure alternatives, there are several reasons someone might still find a need to use telnet today. These range from technical to educational to recreational.
Common Reasons to Use Telnet as a System Administrator
- Legacy Systems and Devices: Older hardware or software systems that haven’t been updated or replaced might only support telnet. Organizations with such systems in place (due to budgetary constraints, specific functionalities, or historical reasons) will still require telnet to access and manage them.
- Testing and Troubleshooting: Network administrators and IT professionals might use telnet as a quick tool to check the availability of TCP ports, ensuring that services are running and listening. It’s a basic way to see if a service is alive on a remote server by attempting a telnet connection to the desired port.
- Network Devices: Some network devices, like older switches, routers, or other peripherals, might have telnet as their primary (or only) interface for management. This is especially true for devices that predate the widespread adoption of SSH.
Using Telnet for Education, Recreation, or Experimentation
- Educational Purposes: Telnet can serve as a teaching tool for students or professionals learning about network protocols, network programming, or the history of the internet. Its simplicity can be advantageous for instructional scenarios where the focus is on understanding core concepts without the complexity of modern security layers.
- Simple Remote Access: In controlled environments, like isolated internal networks with no exposure to external threats, telnet might be used for straightforward remote access without the overhead of encryption.
- Specific Application Needs: Some applications might rely on telnet for specific functionalities. For instance, MUDs (Multi-User Dungeons) — early multiplayer online games — traditionally used telnet for client-server communication.
- Embedded Systems: Some embedded systems or IoT (Internet of Things) devices may use telnet due to its lightweight nature, especially when there’s limited computational power or memory.
- Transitioning Phases: Companies migrating to modern systems might temporarily maintain telnet access as they phase out older hardware or software. This allows them to manage both old and new systems concurrently during the transitional period.
However, it’s crucial to note that if telnet is used, especially in environments with sensitive data or exposure to external networks, it’s vital to be aware of its security limitations. Using it securely might entail additional protective measures, like VPNs or firewall configurations, to minimize the risks.
Leave a Reply
Leave a Reply
