What is Encrypted DNS Traffic?

To help protect your security and privacy, it’s important to understand encrypted DNS traffic and why it matters.
In the vast, interconnected realm of the internet, the Domain Name System (DNS) acts as a pivotal guide, translating human-friendly domain names like ‘example.com’ into IP addresses that machines understand. Every time you visit a website or send an email, a DNS query is made, serving as a bridge between human intent and machine action. However, for years, these DNS queries have been exposed and transmitted in plaintext, making them a goldmine for snoopers, hackers, and even some Internet Service Providers (ISPs) seeking insights into users’ internet behaviors. Enter the concept of “encrypted DNS traffic,” which aims to shield these vital lookups, encapsulating them in layers of cryptographic protection.
The Trouble With Traditional DNS
Before diving into a description of encrypted DNS traffic, we should probably talk about DNS traffic in general. The Domain Name System (DNS) stands as a linchpin in our digital realm. Think of it as an intricate directory for the Internet; its role is not just making online navigation intuitive for users but also augmenting the resilience of online services.
At its core, the DNS bridges the gap between human-friendly and machine-friendly Internet address formats. For an everyday user, instead of recalling a complex IP (Internet Protocol) address like “104.25.98.13” (representing its IPv4 address) or 2400:cb00:2048:1:6819:630d (the IPv6 format), one can simply input ‘groovypost.com’ into a browser.
While for humans, the benefit is clear, for applications and devices, the function of DNS takes a slightly different shade. Its value isn’t necessarily in aiding memory—after all, software doesn’t grapple with forgetfulness as we do. Instead, DNS, in this case, fortifies resilience.
How, you ask? Through DNS, organizations aren’t confined to a single server. Instead, they can disperse their presence over a multitude of servers. This system empowers DNS to direct a user to the most optimal server for their needs. It may lead a user to a server in proximity, eliminating the likelihood of a sluggish, lag-prone experience.
This strategic direction is a cornerstone for most cloud services, where DNS plays a pivotal role in linking users to a nearby computational resource.
Privacy Concerns in DNS
Unfortunately, DNS constitutes a potentially major privacy concern. Without some form of encryption to provide a protective shield for your device’s communication with the DNS resolver, you run the risk of unwarranted access or alterations to your DNS exchanges.
This encompasses intrusions from individuals on your Wi-Fi, your Internet Service Provider (ISP), and even intermediaries. The ramifications? Compromised privacy, as outsiders discern the domain names you frequent.
At its core, encryption has always championed a secure and private internet browsing experience. While discerning that a user accessed ‘groovypost.com’ might seem trivial, in a grander context, it becomes a portal to understanding a person’s online behavior, predilections, and, potentially, objectives.
Such gleaned data can metamorphose into commodities, sold to entities for financial gain or weaponized by malevolent actors to orchestrate fiscal subterfuge.
A report curated by the Neustar International Security Council in 2021 illuminated this threat, revealing that a staggering 72% of enterprises faced at least one DNS incursion in the preceding year.
Furthermore, 58% of these enterprises experienced significant aftermaths from the incursions. As DNS transgressions surge, encrypted DNS traffic emerges as a bulwark against an array of threats, including espionage, spoofing, and various sophisticated DNS stratagems.
Encrypted DNS Traffic: A Deep Dive


Encrypted DNS traffic transforms transparent DNS data into a secure format, decipherable solely by the communicating entities: the DNS client (like browsers or network devices) and the DNS resolver.
The Evolution of DNS Encryption
Originally, DNS wasn’t embedded with security attributes. The birth of DNS came at a time when the Internet was nascent, devoid of online commerce, banking, or digital storefronts. DNS encryption seemed redundant.
However, as we pivot to today’s landscape – marked by a flourishing of e-businesses and an upswing in cyber threats – the need for more security over the privacy of DNS has become clear.
Two prominent encryption protocols have emerged to address this need: DNS over TLS (DoT) and DNS over HTTPS (DoH).
DNS over TLS (DoT)
DoT employs the Transport Layer Security (TLS) protocol to safeguard and encapsulate DNS dialogues. Intriguingly, TLS—commonly recognized by another moniker, SSL—powers HTTPS website encryption and authentication.
For DNS interactions, DoT leverages the user datagram protocol (UDP), coupled with TLS protection. The driving ambition? Amplify user privacy and thwart potential malicious actors aiming to intercept or modify DNS data.
Port 853 stands as the predominant port amongst digital denizens for DoT. Advocates of the DoT standard often assert its potency in grappling with human rights challenges in tumultuous regions.
Nonetheless, in nations where free expression faces curtailment, DoT’s protective aura might ironically spotlight users, making them targets for suppressive regimes.
DNS over HTTPS (DoH)
DoH, in its essence, utilizes HTTPS for remote DNS interpretations and primarily operates via port 443. For successful operation, resolvers need a DoH server hosting a query endpoint.
The Adoption of DOH Across Browsers
Since Google Chrome version 83 on both Windows and macOS, the browser has embraced DoH, accessible via its settings. With the right DNS server setup, Chrome accentuates DNS requests with encryption.
Moreover, everyone holds the autonomy to choose their preferred DoH server. Chrome even integrates with various DoH providers, such as Google Public DNS and Cloudflare.
Microsoft Edge also provides built-in support for DoH, navigable through its settings. When activated and paired with a compatible DNS server, Edge ensures DNS queries remain encrypted.

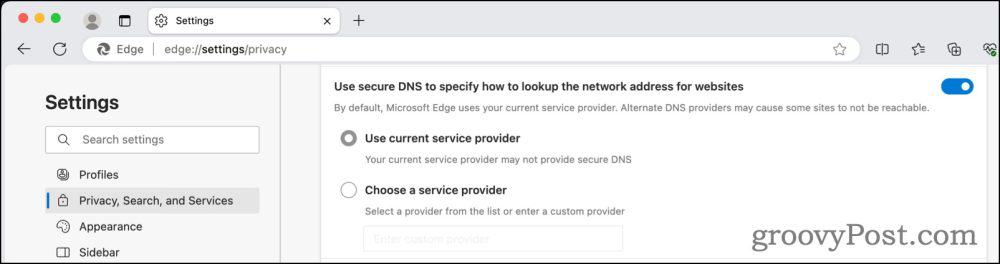
In a collaborative venture with Cloudflare in 2018, Mozilla Firefox integrated DoH, known as the Trusted Recursive Resolver. From February 25, 2020, U..S-based Firefox aficionados could harness DoH with Cloudflare acting as the default resolver.
Not to be left out, Opera users can also toggle DoH on or off via the browser’s settings, directing DNS requests towards Cloudflare by default.
The Integration of DOH With the Operating System
Historically, Microsoft’s operating systems have hesitated to embrace avant-garde tech. Windows 10, however, veered towards the future, allowing users to activate DoH via its settings.

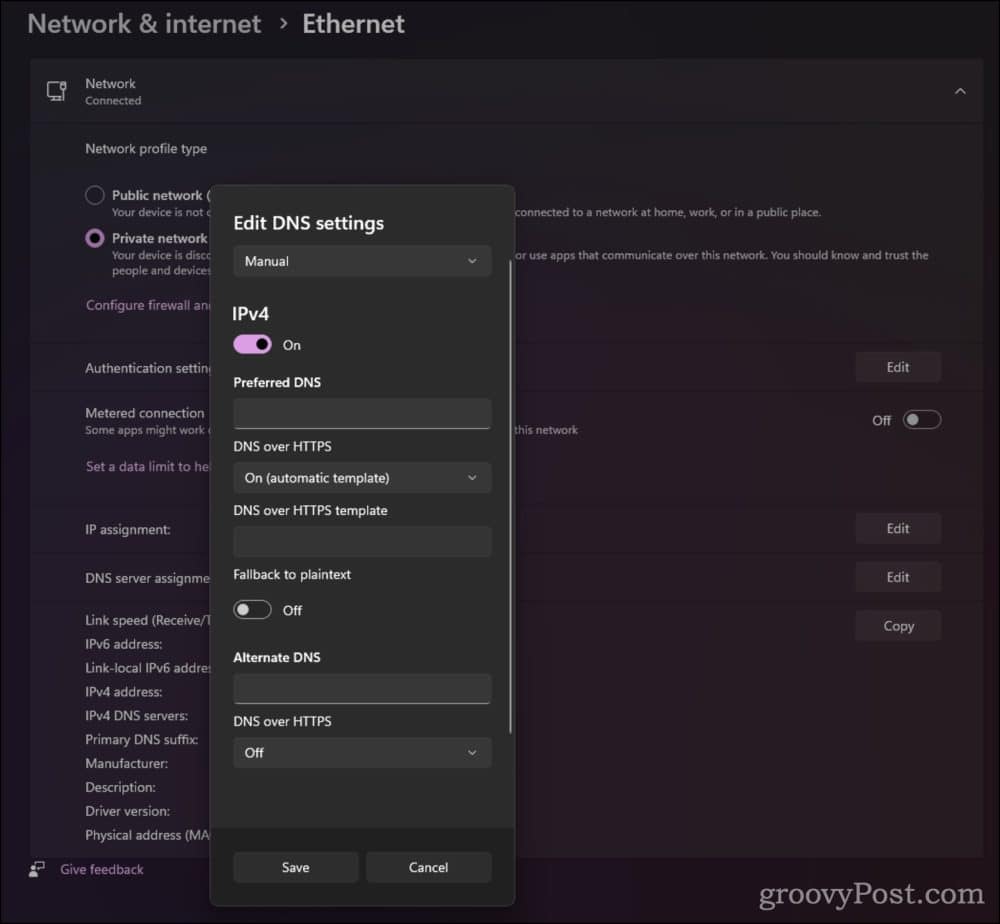
Apple has ventured further, introducing app-centric encryption techniques. This groundbreaking move empowers app developers to incorporate their distinct encrypted DNS configurations, sometimes rendering traditional controls obsolete.
The expansive horizon of encrypted DNS traffic symbolizes the evolution of the digital realm, emphasizing the perpetual quest for fortified security and enhanced privacy.
The Controversy Accompanying Encrypted DNS
While encrypting DNS traffic bolsters confidentiality and enhances user privacy with protective measures such as ODoH, not everyone supports this shift. The divide primarily lies between end-users and network operators.
Historically, network operators accessed DNS queries to thwart malware sources and other undesirable content. Their endeavor to uphold these practices for legitimate security and network management needs is also the focal point of the IETF ADD (Adaptive DNS Discovery) working group.
In essence, the debate can be characterized as: “universal encryption” versus “network sovereignty”. Here’s a detailed exploration:
Universal DNS Traffic Encryption
The majority of encryption methods hinge on DNS resolvers that are configured for encryption. However, these encryption-supporting resolvers comprise only a tiny fraction of the total.
Centralization or consolidation of DNS resolvers is a looming issue. With limited options, this centralization creates tempting targets for malevolent entities or intrusive surveillance.
Most encrypted DNS configurations allow users to choose their resolver. However, making an informed choice can be daunting for the average individual. The default option might not always be optimal due to various reasons like the resolver’s host jurisdiction.


Gauging the reliability of centralized server operators is intricate. Often, one has to depend on their public privacy declarations and potentially their self-evaluations or third-party assessments.
External reviews aren’t always robust. Predominantly, they base their conclusions on data given by the auditees, forgoing an in-depth, hands-on investigation. Over time, these audits might not accurately reflect an operator’s practices, especially if there are organizational changes.
Encrypted DNS is but one facet of internet browsing. Multiple other data sources can still track users, making encrypted DNS a mitigation method, not a cure-all. Aspects like unencrypted metadata remain accessible and informative.
Encryption might shield DNS traffic, but specific HTTPS connection segments remain transparent. Additionally, encrypted DNS can circumvent DNS-based blocklists, albeit accessing sites directly via their IP does the same.
To genuinely counter tracking and oversight, users should explore comprehensive solutions like virtual private networks (VPNs) and Tor, making traffic scrutiny more challenging.
The Stance of ‘Network Sovereignty’
Encryption could curtail an operator’s capability to scrutinize and subsequently regulate or rectify network operations. This is pivotal for functionalities like parental controls, corporate DNS query visibility, and malware detection.
The ascension of Bring Your Own Device (BYOD) protocols, permitting users to interact with secured systems using personal devices, introduces complexities, especially in stringent sectors like finance and healthcare.
In summary, while encrypted DNS offers enhanced privacy and security, its adoption has sparked a spirited debate, highlighting the intricate balance between user privacy and network management.
The Wrap-Up: Rely Upon Encrypted DNS Traffic or View It As One Privacy Tool
In an age of escalating cyber threats and increasing privacy concerns, safeguarding one’s digital footprint has never been more critical. One of the foundational elements in this digital frontier is the Domain Name System (DNS). Traditionally, though, these DNS requests were conducted in plain text, exposed to any prying eyes that might be looking, be it cybercriminals or overreaching third parties. Encrypted DNS traffic has emerged as a solution to bridge this vulnerability.
It’s up to you to determine the best way to use encrypted DNS. You could rely on a software solution, like the browser features offered by Microsoft Edge, Google Chrome, and others. If you use OpenDNS on your router, though, you should also consider pairing it with DNSCrypt for all-around security.
Leave a Reply
Leave a Reply
